
How to Use KMS: Examples, Pinouts, and Specs
 Design with KMS in Cirkit Designer
Design with KMS in Cirkit DesignerIntroduction
The KMS (Key Management Service), manufactured by MKS with the part ID OSC V1.0, is a cloud-based service designed to manage cryptographic keys for applications and services. It ensures secure data encryption and access control, making it an essential component for safeguarding sensitive information in modern digital systems.
Explore Projects Built with KMS
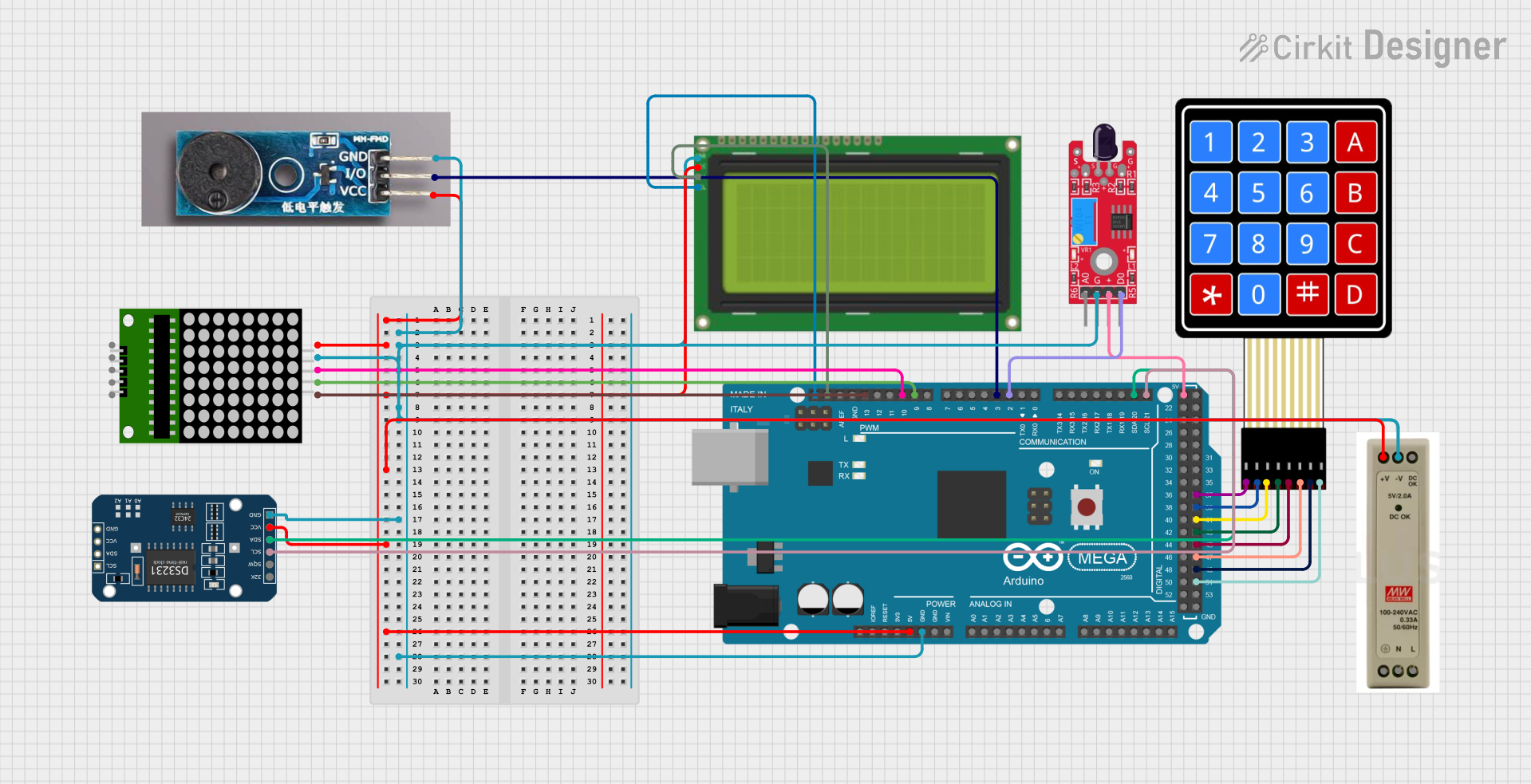
 Open Project in Cirkit Designer
Open Project in Cirkit Designer
 Open Project in Cirkit Designer
Open Project in Cirkit Designer
 Open Project in Cirkit Designer
Open Project in Cirkit Designer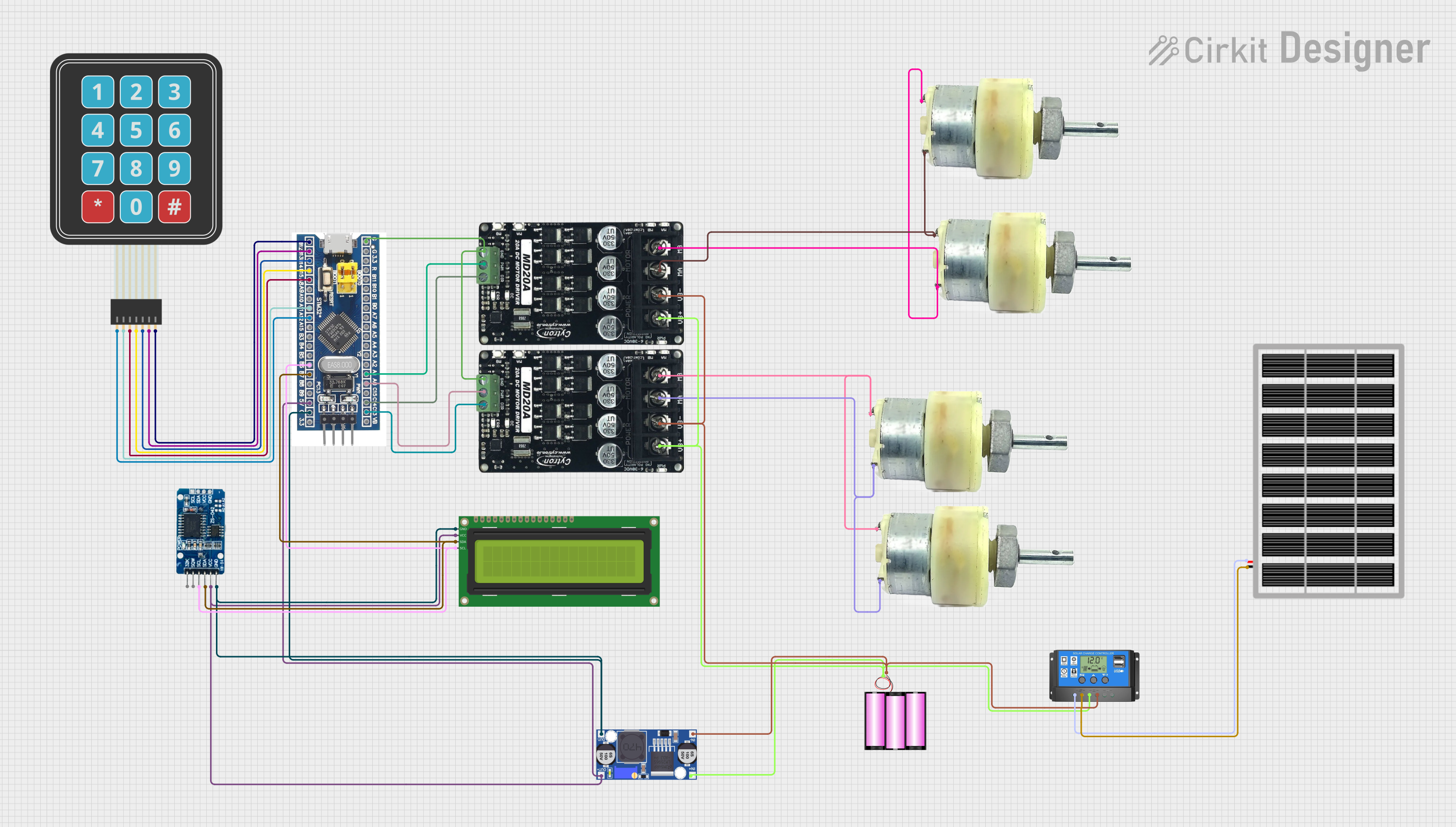
 Open Project in Cirkit Designer
Open Project in Cirkit DesignerExplore Projects Built with KMS

 Open Project in Cirkit Designer
Open Project in Cirkit Designer
 Open Project in Cirkit Designer
Open Project in Cirkit Designer
 Open Project in Cirkit Designer
Open Project in Cirkit Designer
 Open Project in Cirkit Designer
Open Project in Cirkit DesignerCommon Applications and Use Cases
- Data Encryption: Encrypting sensitive data at rest or in transit.
- Access Control: Managing permissions for accessing encrypted data.
- Cloud Security: Securing cloud-based applications and services.
- Compliance: Meeting regulatory requirements for data protection.
- IoT Security: Protecting data in Internet of Things (IoT) devices.
Technical Specifications
The KMS (OSC V1.0) operates as a virtual service rather than a physical electronic component. However, its integration into systems requires understanding its key parameters and API-based interaction.
Key Technical Details
| Parameter | Description |
|---|---|
| Service Type | Cloud-based Key Management Service |
| Encryption Standards | AES-256, RSA-2048, RSA-4096, ECC |
| API Protocol | RESTful API over HTTPS |
| Authentication | API Key, OAuth 2.0, or IAM (Identity and Access Management) integration |
| Latency | < 50ms for key generation and encryption operations (region-dependent) |
| Scalability | Supports millions of keys and operations per second |
| Compliance | Meets standards like GDPR, HIPAA, PCI DSS, and FIPS 140-2 |
API Endpoints
| Endpoint | Description |
|---|---|
/generateKey |
Generates a new cryptographic key |
/encrypt |
Encrypts data using a specified key |
/decrypt |
Decrypts data using a specified key |
/listKeys |
Lists all keys available in the service |
/deleteKey |
Deletes a specified key |
Usage Instructions
To use the KMS (OSC V1.0) in your application, follow these steps:
Step 1: Set Up the Service
- Create an Account: Sign up for the MKS cloud platform and enable the KMS service.
- Generate API Credentials: Obtain an API key or configure OAuth 2.0 for secure access.
- Configure IAM Policies: Define roles and permissions for users and applications.
Step 2: Integrate the API
Use the provided RESTful API to interact with the KMS. Below is an example of how to generate a key and encrypt data using Python:
import requests
Define the API base URL and your API key
BASE_URL = "https://api.mks-kms.com/v1" API_KEY = "your_api_key_here"
Headers for authentication
headers = { "Authorization": f"Bearer {API_KEY}", "Content-Type": "application/json" }
Step 1: Generate a new key
generate_key_url = f"{BASE_URL}/generateKey" response = requests.post(generate_key_url, headers=headers) if response.status_code == 200: key_id = response.json().get("keyId") print(f"Key generated successfully. Key ID: {key_id}") else: print(f"Failed to generate key. Error: {response.text}")
Step 2: Encrypt data using the generated key
encrypt_url = f"{BASE_URL}/encrypt" data_to_encrypt = {"keyId": key_id, "plaintext": "Hello, World!"} response = requests.post(encrypt_url, json=data_to_encrypt, headers=headers) if response.status_code == 200: ciphertext = response.json().get("ciphertext") print(f"Data encrypted successfully. Ciphertext: {ciphertext}") else: print(f"Failed to encrypt data. Error: {response.text}")
Step 3: Best Practices
- Secure API Keys: Store API keys securely using environment variables or a secrets manager.
- Rotate Keys Regularly: Periodically generate new keys to enhance security.
- Monitor Usage: Use logging and monitoring tools to track key usage and detect anomalies.
- Limit Permissions: Follow the principle of least privilege when assigning roles and permissions.
Troubleshooting and FAQs
Common Issues and Solutions
Issue: API requests return a 401 Unauthorized error.
- Solution: Verify that your API key or OAuth token is correct and has not expired. Ensure the IAM policies allow access to the requested operation.
Issue: High latency during encryption or decryption.
- Solution: Check the region of your KMS instance and ensure it is close to your application. Use caching for frequently accessed keys.
Issue: Key deletion fails with a "Key in use" error.
- Solution: Ensure the key is not being used by any active encryption or decryption operations. Revoke access before attempting deletion.
Issue: Data decryption fails with "Invalid ciphertext" error.
- Solution: Verify that the correct key ID is being used for decryption. Ensure the ciphertext has not been tampered with.
FAQs
Q: Can I use KMS for non-cloud applications?
A: Yes, KMS can be integrated into on-premises applications via its API.Q: What happens if I lose access to a key?
A: If a key is deleted or access is lost, any data encrypted with that key cannot be decrypted. Always back up critical keys.Q: Is KMS suitable for real-time applications?
A: Yes, KMS is optimized for low-latency operations, making it suitable for real-time use cases.Q: How do I ensure compliance with regulations?
A: KMS is compliant with major standards like GDPR and HIPAA. Use its logging and auditing features to maintain compliance records.
This documentation provides a comprehensive guide to using the KMS (OSC V1.0) service effectively. For further assistance, refer to the MKS support portal or contact their technical support team.